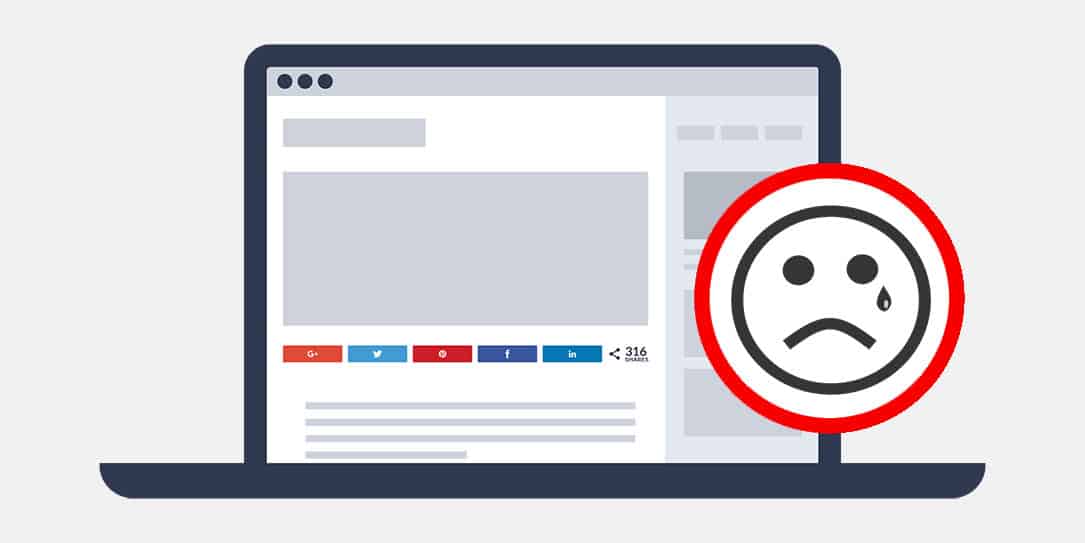
Well, this most certainly is how we wanted to start out our Friday morning — dealing with a WordPress plugin exploit. I’m sure you can sense the sarcasm… on that note, we’d like to first apologize if you visited our website at some point overnight and were re-directed to another site, especially if it contained adult content as some of our users have complained about.
Social Warfare zero-day exploit
First, the technical bit.
NOTE: IF YOU RUN SOCIAL WARFARE AND HAVEN’T UPDATED TO 3.5.3 YET, DO IT NOW!
The WordPress plugin that was affected turned out to be one that we’ve used for a few years now: Social Warfare. In this day and age, social reach is important for spreading articles and getting traffic to websites. Like many decent plugins, this one does get frequent updates. However, the 3.5.2 update on March 19th contained a Cross-Site Scripting (XSS) vulnerability, as reported on by Wordfence:
Earlier today, an unnamed security researcher published a full disclosure of a stored Cross-Site Scripting (XSS) vulnerability present in the most recent version of popular WordPress plugin Social Warfare. The plugin, which was subsequently removed from the WordPress.org plugin repository, has an active install base of over 70,000 sites. The flaw allows attackers to inject malicious JavaScript code into the social share links present on a site’s posts.
Wordfence
Basically, in a nutshell, this zero-day exploit — which potentially affected over 70,000 websites — allowed attackers to “inject malicious JavaScript code into the social share links present on a site’s posts.” Sites that were infected, like ours, ended up seeing visitors redirected to other sites (including sites with adult content).
Once discovered, the Social Warfare team was quick to release the 3.5.3 update which basically rolled back the changes made in 3.5.2. However, the plugin Changelog simply indicated the update was an “Immediate security patch for 3.5.x” without further information.
Credit where credit is due, Social Warfare did work on and get a fix/rollback up fairly quickly.
How it affected Techaeris (and you)
Now for the “editorial” part. As mentioned above, the staff here at Techaeris would like to, once again, apologize to those who tried to visit our site and were redirected elsewhere as a result of this exploit.
When we woke up this morning, we noticed our view counts were WAY down… like non-existent. When visiting the site, we were immediately redirected off-site which explained the lack of traffic. When we took a closer look, Social Warfare was the only plugin that needed updating. Of course, mentioning a security fix, we updated it and voila! Techaeris.com was back up and running as it should be.
On that note, we tried to find out exactly what the issue was. We hit up the WordPress forums and found this locked post about this issue, but we were still left in the dark as to what exactly the exploit was. While investigating the issue further, we found that they did post to Twitter yesterday about the exploit:
WE ARE AWARE OF A ZERO-DAY EXPLOIT AFFECTING SOCIAL WARFARE CURRENTLY BEING TAKEN ADVANTAGE OF IN THE WILD. Our developers are working to release a patch within the next hour. In the meantime, we recommend disabling the plugin. We will update you as soon as we know more.
— Warfare Plugins (@warfareplugins) March 21, 2019
That being said, even if you follow them on Twitter, given the sheer volume of tweets in a day, it’s easy to miss. On that note, they also sent out an email alerting users. However, that email came much later after the tweet was sent out. Given that we are a very small team here, both the Tweet and email were missed as it was later in the evening.
At any rate, when you run a website, a certain level of trust extends to the developers of plugins you run to help enhance your website, especially when you are paying for premium plugins. When you’re running plugins that 70,000 other websites are running, that trust factor gains a sort of implied additional trust. Sure, mistakes happen, and sure Social Warfare was relatively quick with a fix once they were made aware of the exploit. But, unfortunately, that earned trust has been broken and we will be moving on.
So, on that note, we’ve disabled Social Warfare and are actively looking for a replacement social media so in the meantime, you may notice a lack of social sharing buttons on our site.
Are you also a site owner who was affected by the Social Warfare exploit? Were you one of our users who was inadvertently redirected (again, our apologies)? Let us know in the comments below or on Twitter, or Facebook. You can also comment on our MeWe page by joining the MeWe social network.
Last Updated on May 6, 2021.