The use of “digital signatures” has exploded during the pandemic. Around the globe, people have changed how they travel, transact, and work. In the manufacturing sector, organizations have gravitated to hybrid work environments. In all of these cases, digital signatures are being used to protect digital interactions as well as digital assets, from documents to software code.
Estimated reading time: 5 minutes
Unfortunately, all of these digital assets remain at risk since the signature’s certificate may have actually expired or been revoked. Fraudsters can make these certificates appear as though they were still valid. But their changes and forgeries can be combatted using timestamping services that bring trust to digital signatures.
The Risk Timeline
There is a time-based workflow associated with digital signatures that is best understood by reviewing the workflow for a traditional ink signature. Whenever a legal document is signed, a notary is typically present. The notary’s job is three-fold. First there must be verification of the identity of the person who is signing. Second, the notary must validate the date and time of the signature. After these two processes are completed, the third step is recording the signature in a logbook with the date and time of the transaction and a thumbprint.
A version of this flow is used in the digital world. After a document is signed with a public key infrastructure (PKI)-based digital signature, there is a non-repudiation step. Non-repudiation provides proof of the origin of the data and its integrity, making it difficult for, say, the party to a contract or a communication to deny the authenticity of the signature on a document, or that the message was sent in the first place. But this repudiation step cannot necessarily be trusted.
When a PDF document is digitally signed with a PKI based certificate, the information about the person who is signing is added, along with the date and time of the signature. However, this date and time is based on the computer’s local time, which can be changed. This makes it easy for someone to fraudulently manipulate or forge the signature’s date and time. If fraudster can make a digital certificate appear valid, even if it is expired or has been revoked. All that is necessary is to change this local computer time. The only way to trust the digital signature is to ensure that its timestamp can be trusted.
How Trusted Time Stamping Works
Trusted digital identities are needed for a wide variety of applications ranging from authentication and data encryption to document and code signing. PKI digital certificates are used to create them. To establish proof of these signatures’ existence at an instant of time, the Internet Engineering Task Force (IETF) created the PKI Time-Stamp Protocol (TSP).
When this protocol is used, it is not only possible to combat digital certificate forgery and prevent unauthorized use of revoked certificates, but also simplify time-based compliance record-keeping. The use of trusted time stamps also strengthens legal cases and proves the long-term validity of a signature. For instance, antivirus updates can be secured by using signatures with a trusted timestamp.
Without a timestamp, signatures will expire or invalidate when the certificate expires or is revoked. End users will be warned that they should not trust the code. But with a timestamp and long-term validation, the signature will still be trusted since the signing certificate was valid when the signature was applied.
Accurate and trusted timestamps are applied to a digital signature by a Time Stamping Authority. The Time Stamping Authority must meet RFC 3161 requirements established by the IETF. The RFC 3161 Time Stamp Protocol proves there has been no tampering with the data. Using a Time Stamping Authority while signing document or code then prevents tampering with the Timestamp.
The process is as follows: First, the client application (Microsoft Authenticode or Signtool, as examples) creates a hash of the document or code file. The has is a unique identifier of the data or file that needs to be timestamped. This hash is sent it to the Time Stamping Authority, which combines the hash of the file with a trusted timestamp and signs it with a private key. A timestamp token is then created and returned to the client. The timestamp token contains the information the client application will need to verify the timestamp later. The process concludes with recording the timestamp token within the file.
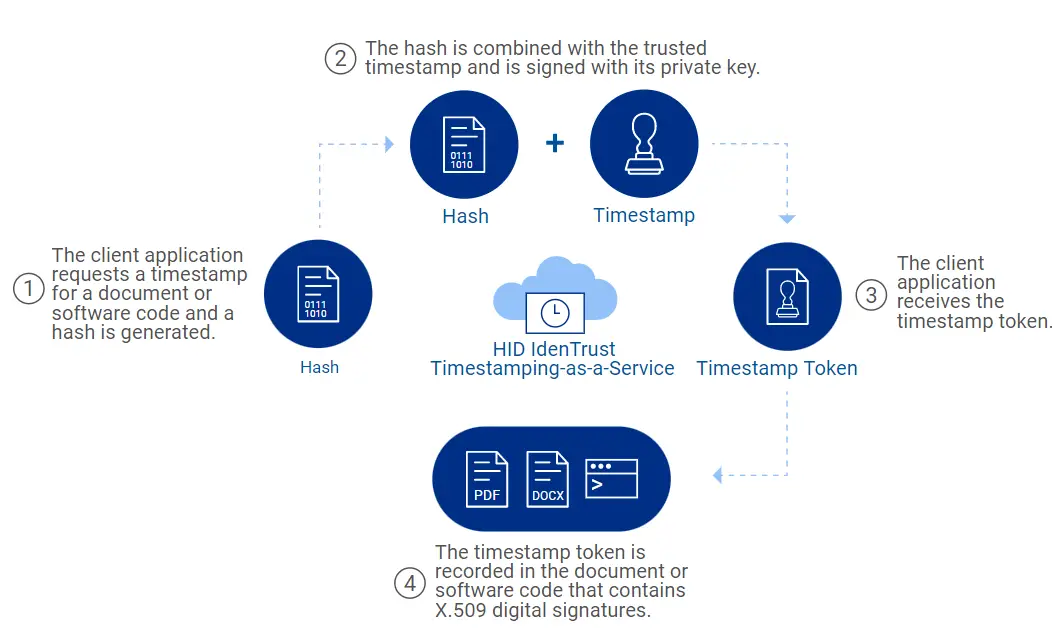
When the resulting timestamped data or file is later opened, the client application will use the Time Stamping Authority’s public key to validate that the timestamp came from a trusted Time Stamping Authority and re-calculate a hash of the original data. This new hash is compared to the originally created hash. The hash check will fail if any changes have been made to the data since the timestamp was applied, this hash check. Warning messages will also be shown saying that the data has been altered and the timestamp should not be trusted.
In many use cases this process must be executed at very high throughput rates. An example is antivirus signature file signing or firmware signing – millions of timestamps might need to be applied each week. Trusted timestamping service providers make this easier. They provide enterprises with a high-availability cloud-based platform for embedding timestamps.
These timestamps can be embedded in any software application, documents, or digital files. Any manipulation of the timestamp file is after the signature and timestamp are applied causes a hash value mismatch that breaks the file’s seal and alerts the user that the file can no longer be trusted. It is no longer in its original state and the data is altered. Trusted timestamps are vital to the integrity of digital signatures because they are applied using independently verified and auditable date and Coordinated Universal Time (UTC) sources.
Because they are not subject to tampering like a local system clock is, they foster certainty about the application of a digital signature. Trusted timestamping will continue to see growing demand among users to verify the date and time of their electronically or digitally signed documents, code, and other files. Doing so can prevent forgery while also create longevity for these digital signatures, even after expiration, through long-term validation and non-repudiation of their time and date.
By Mrugesh Chandarana, Director Product Management, Identity, and Access Management Solutions, HID Global
What do you think of digital signatures? Please share your thoughts on any of the social media pages listed below. You can also comment on our MeWe page by joining the MeWe social network.










