Another day, another vulnerability found in iOS 8.1.1 that allows nefarious individuals to steal information from your iPhone. This time, researchers at FireEye have dubbed this strain “Masque Attack,” as the rogue software is able to imitate, or mask many of the applications on an iOS device. As is often the case, it should be pretty easy to avoid this malware, but keep reading to see just how nasty Masque Attack can be.
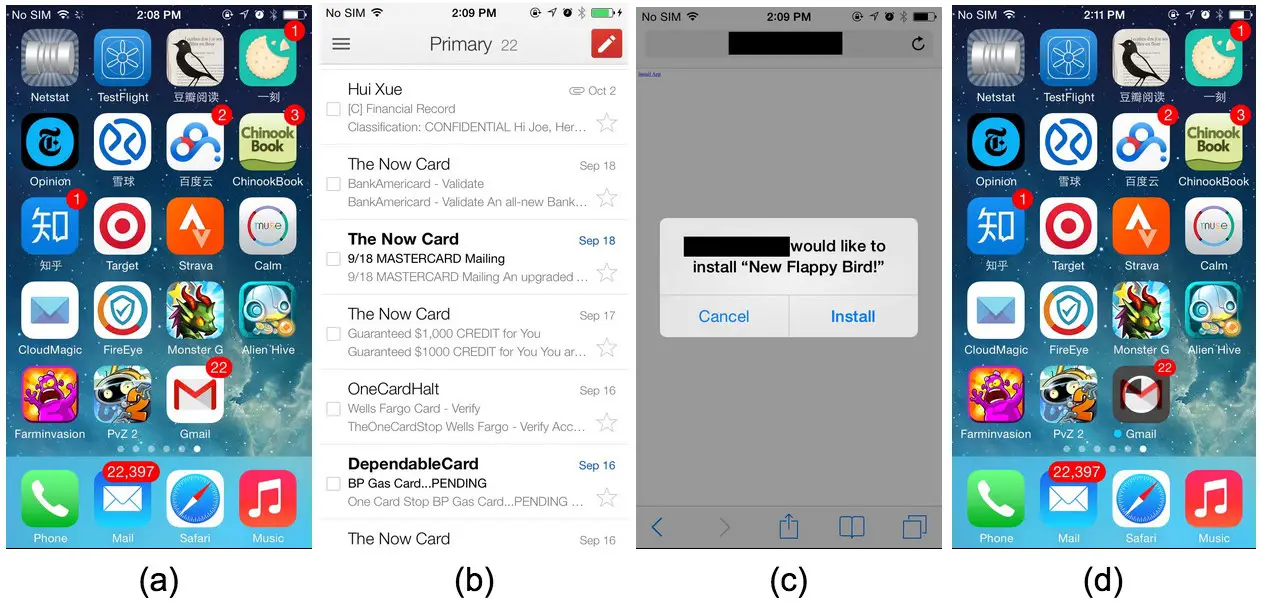
This malware exploits a hole in iOS where an app is not vetted as long as it has the same bundle identifier as the app it is replacing. In this instance, the app’s certificate isn’t checked because the bundle identifiers match. This malware arrives on an infected device in the same way that many other mobile exploits are spread: Phishing. In the example provided by FireEye, a user might receive a text message with a link telling them about a great new version of Flappy Bird. Since everybody wants to play Flappy Bird, the user of course clicks on the link, sending them to a page prompting them to install.
Unfortunately, the user isn’t getting a new copy of Flappy Bird, the app is instead updating one of nearly any of the apps on your iOS device. This vulnerability cannot update stock iOS apps, however it can replace nearly anything else including e-mail, banking apps, etc. Once the new app is installed, it is virtually indistinguishable from the legitimate app. In FireEye’s example video below, they were kind enough to place a warning text at the top of the app. Chances are good that most everybody trying to use this exploit for personal gain won’t be quite so nice.
As noted in the video, once the app has been replaced, it will start to funnel your personal information to another system. In the example above it was e-mail, but it could just as easily be online banking credentials, or social network logins, etc.
Masque Attack is particularly frightening because it can be transmitted not only via a USB connected phone, but it can also be downloaded wirelessly. FireEye was able to take advantage of this exploit on iOS 7.1.1, 7.1.2, 8.0, 8.1 and 8.1.1 beta, on both jailbroken and stock iPhones. The good guys over at FireEye have also notified Apple of this vulnerability, so it will hopefully be patched in the near future.
So, what can you do to avoid the Masque Attack until then? First and most importantly – Install apps from iTunes. Apple has a pretty good lock on apps coming directly from the App Store. Second, if you’re going to sideload any sort of app, be sure you know exactly where the app is coming from, and be sure that you know and trust the source. With a few precautions, and a bit of common sense, you should have no problem avoiding this vulnerability until it gets patched.
[button link=”http://www.fireeye.com/blog/technical/cyber-exploits/2014/11/masque-attack-all-your-ios-apps-belong-to-us.html” icon=”fa-external-link” side=”left” target=”blank” color=”285b5e” textcolor=”ffffff”]Source: FireEye[/button][button link=”http://www.dazeinfo.com/2014/11/11/apple-inc-aapl-masque-attack-iphone-ipad-ios-malware-attack/” icon=”fa-external-link” side=”left” target=”blank” color=”285b5e” textcolor=”ffffff”]VIA: DazeInfo[/button]Last Updated on November 27, 2018.










Comments are closed.