The world of information security was certainly a whirlwind of activity in 2017. It seemed no one was immune to some sort of security breach or incident and it only got worse through the year. Some of the affected companies involved in incidents are still paying the price for those breaches. The list below is just some of the cybersecurity incidents that took place in 2017.
- Uber announces cybersecurity incident that affects 57 million users.
- BadRabbit cripples Eastern European countries.
- Disqus suffers breach that affects millions.
- Yahoo reveals 3-billion accounts were hacked.
- Whole Foods hit by a security breach.
- Sonic Drive-In hit by a data breach.
- Imgur reports data breach that occurred in 2014.
- Equifax hackers demand $2.6 million USD.
- Verizon data leak exposes up to 6 million accounts.
That’s just a short list of information security incidents in 2017 and we probably don’t know about many others. With 2018 coming, the landscape for information security is wide open. We’re lucky enough to have a group of information security experts who are making some predictions for the industry in 2018. Check out their commentary below and the infographic that follows. Thanks to LogRhythm Labs for the information security infographic!
Domingo Guerra, co-founder and president of Appthority:
Enterprise Data via Mobile Is the Next Frontier for Cyber Criminals
Hackers will progress from small footprint ‘front door’ malware and Man-in-the-Middle attacks to attacks that access all of an app’s or a company’s data via the ‘backdoor’ – app vulnerabilities. The next big breach won’t happen because hackers take over a single phone—it will happen because they gain access to massive amounts of sensitive corporate data collected by the apps. Indeed, the next massive Equifax-style breach could be a mobile breach.
The problem is that mobile apps collect a large amount of valuable data, data that may not even be necessary for the app’s use, such as specifics about the user’s physical location, all the contacts, or access to their cloud storage accounts. This data may be stored on the device, offloaded for processing to the cloud, shared with third parties, and even leaked through poor encryption and developer practices.
So, while the focus is on breaches to corporate systems via compromised user credentials or web apps, 2018 will be the year that the public realizes what hackers already know, enterprise data is available for the taking, in massive amounts, via leaky mobile apps. In fact, it just happened to Uber, where hackers stole the data of almost 60 million users and drivers because they found the Uber developer’s username and password to access Uber data stored in an Amazon server. That’s why forward-thinking organizations are putting the proper mobile defenses in place—before they become the next Equifax or Uber.
Tom Kemp, CEO of Centrify:
Organizations will respond to the current threat landscape with a Zero Trust Model.
The big event of 2017 was the Equifax breach, where cybercriminals gained access to the data of 143 million people. The fallout included the departure of senior executives, the filing of more than 23 class-action lawsuits and a 35 percent stock price decline that wiped out $4 billion in market cap. The unusually severe market reaction may indicate investors are growing increasingly intolerant of companies that don’t take security seriously. We expect companies to respond by implementing Zero Trust Models—which involves two important shifts. First, it shifts access controls from the perimeter to individual devices and users, thereby allowing employees to work securely from any location without the need for a traditional VPN. Secondly, access to services is granted based on what is known about a user and their device, which are all authenticated and authorized.
The security market will incorporate machine learning to address identity-related breaches.
Last year, companies including Centrify integrated machine learning to ascertain the risk level of individual transactions and decide in real-time whether or not to allow them. While behavior analytics aren’t new until now few solutions had the ability to actually stop a transaction in real time. This pivots identity security away from detect-and-respond alerts and towards more automated preventative controls. For example, risk-based authentication (RBA) improves user experience by using machine learning algorithms to assess risk and can require a second factor of authentication only when risk is high. The benefits are substantial, and we expect to see the rapid integration of these technologies into cybersecurity solutions in 2018.
The dark but lucrative trend in ransomware will continue to explode in the coming year.
According to sources, between 2016 and 2017 (to date), dark web ransomware sales grew 2,500 percent to $6.2 million. According to the FBI, 2016 ransom payments totaled about $1 billion, up from $24 million in 2015. While we predicted increases in ransomware last year, this off-the-charts growth surprised even us. We expect this lucrative trend to continue for many years to come.
The rapid move to the cloud will increase the adoption of zero-trust network models and modern microservices architectures which will mandate the use of least privilege.
In 2017, companies moved huge segments of their infrastructures into the cloud. Security considerations there are similar to those on premises: authentication is still required and privileges must be managed. We anticipate the widespread adoption of technologies designed to manage privileged identities with extreme granularity. Least privilege will become an increasingly common term around the datacenter.
Automation frameworks will make it easier for DevOps to adopt AWS securely.
In 2018, security vendors will continue to embrace Amazon’s shared responsibility model for AWS, recognizing that scalable automation is essential to protect sensitive information in the cloud. This will result in the rise of DevOps, a fast-growing segment required for successful automation due to its ability to script, automate, scale and handle exceptions effectively. Increased, straight-forward automation will make it easier for DevOps to adopt AWS securely. In turn, baking security into the process will allow for further adoption of cloud-based services.
Blockchain will emerge as a potential disruptor across many areas of technology
Blockchain technology has started making serious waves–and not just in the world of cryptocurrencies. Even US defense contractor Lockheed Martin seems to be exploring blockchain-related cybersecurity options. While we expect blockchain to emerge as a potential disruptor across many areas of technology in 2018, it will take several years before vulnerabilities can be addressed and the technology is considered mature enough to act as a basis for enterprise security.
Increasing identity-related breaches and vendor fatigue will force organizations to reevaluate their entire security postures — architecture, budget and project priorities.
According to Verizon’s annual Data Breach Investigations Report (DBIR), in 2015, compromised identities were responsible for 50 percent of all data breaches. That number grew to 66 percent in 2016, and 81 percent in 2017. Attackers are focusing on the most vulnerable areas of the business–identities.
Still, most organizations aren’t making the connection. In 2017, companies will spend just 4.7% of their total security budgets on identity and access management (IAM)—the very technology that could help prevent four out of five breaches. In 2018, a combination of increasing identity-related breaches and security vendor fatigue will force companies to reevaluate their entire security postures, from the ground up.
However, in the meantime, unfortunately, things will get worse before they get better– but new models such as Zero Trust and a focus on securing identities provide a path forward to turning the cybersecurity tide.
 LogRhythm Labs:
LogRhythm Labs:
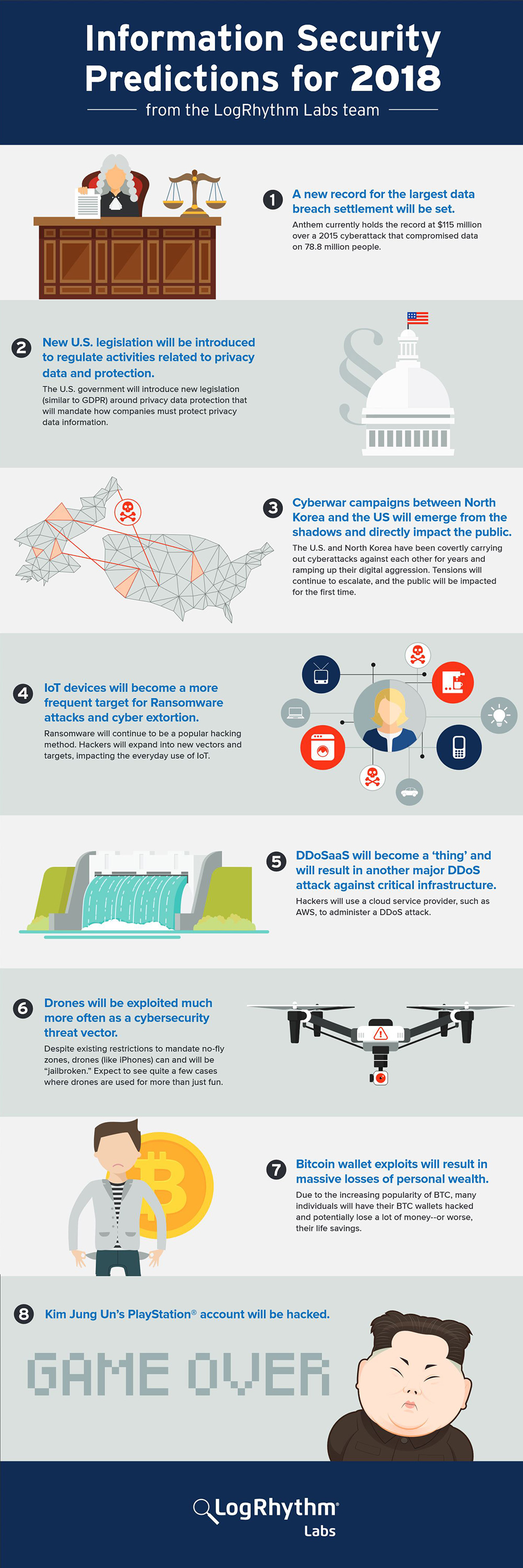
A new record for the largest data breach settlement will be set.
Anthem currently holds the record at $115 million over a 2015 cyberattack that compromised data on 78.8 million people.
New U.S. legislation will be introduced to regulate activities related to privacy data and protection.
In response to the continued fallout from the Equifax breach, the U.S. government will introduce new legislation (similar to GDPR) around privacy data protection that will mandate how companies must protect privacy data information.
Cyberwar campaigns between North Korea and the United States will emerge from the shadows and escalate, directly impacting the public for the first time.
The U.S. and North Korea have been carrying out cyberattacks against each other for years and ramping up their digital aggression. Largely in private. Tensions will continue to escalate, and the public will be impacted for the first time.
IoT devices will become a more frequent target for Ransomware attacks and cyber extortion.
Ransomware will continue to be a popular hacking method. Hackers will expand into new vectors and targets, impacting the everyday use of IoT.
Drones will be exploited much more often as a cybersecurity threat vector.
Despite existing restrictions to mandate no-fly zones, drones, like iPhones, can and will be “jailbroken.” Expect to see quite a few cases where drones are used for more than just fun.
DDoSaaS will become a ‘thing’ and will result in another major DDoS attack against critical infrastructure.
Hackers will use a cloud service provider, such as AWS, to administer a DDoS attack.
Bitcoin wallet exploits will result in massive losses of personal wealth.
Due to the increasing popularity of BTC, many individuals will have their BTC wallets hacked and potentially lose a lot of money–or worse, their life savings.
Kim Jong Un’s PlayStation® will be hacked.
 Ray Rothrock, CEO and chairman of RedSeal:
Ray Rothrock, CEO and chairman of RedSeal:
Now that all of our personal information and data is in the ether, in 2018, criminals will assimilate the disparate pieces into full cyber clones, which they’ll use – like White Walkers or Storm Troopers – to overwhelm consumer banking systems.
The first $1B claim against a cyber insurance policy will be filed. As a result, providers will take a page from health insurance’s playbook and require companies to get cyber check-ups as part of negotiating rates.
Similar to the Richter scale, Cyber Magnitude becomes a new standard for measuring “Net quakes” caused by major breaches. The formula considers – among other things – the number of people affected, the financial impact on the target, the days passed undetected.
What do you think of the 2018 predictions from our information security experts? Do you have your own information security predictions for 2018? What did you think of all the information security issues in 2017? Let us know in the comments below, or on Google+, Twitter, or Facebook.