This guest post was written by Javvad Malik whose full bio can be found at the end of this article. All thoughts and opinions are those of the author and do not reflect on Techaeris or its staff.
You’re probably familiar with the game, marry, date or dump. It’s where you’re given a choice of three people and you have to say out of the three, which one would you choose to marry, date or dump.
It’s a fun game to play with friends, where you usually pick three people out of a particular TV show or movie and choose. For example, you may have to choose between three different actors who played James Bond. So, out of Sean Connery, Pierce Brosnan and Daniel Craig, who would you marry, who would you only date, and who would you dump?
This becomes particularly amusing when presented with three equally unappealing choices. It forces you to think of your priorities and what is important to you. Sometimes you base your decisions on short-term things. Like, say you’re choosing to marry Sean Connery because he’s the oldest and therefore possibly the richest. Or dumping Daniel Craig because his face always resembles someone who just bit into a lemon.
What has this got to do with security I hear you ask? Well, almost everything.
With RSA nearly upon us, those attending, and even those who aren’t will be bombarded with messages about how a vendor can solve all the security problems your organization faces. If your organization is in the market to buy a security product, it is like playing the most complex game of marry, date or dump ever.
What do you want out of (security) life?
Security products and strategy rarely, if ever, are a standalone investment. Rather it forms part of a wider security portfolio.
But, in the big scheme of things, what does a robust security portfolio look like?
Unfortunately, the answer may not be as easy as some may believe.
In 2013, 451 Research Director Wendy Nather published research entitled, “the real cost of security,” in which Nather interviewed dozens of CISOs. The question that was asked of all was:
“I’m a new CISO. It’s my first day on the job in an organization that has never done security before. What should I buy?”
The results highlighted that even the experts can’t agree. Some mentioned as few as four different technologies and others stated as many as 31. Nearly everyone caveated their answers with “it depends”.
Interestingly, the minimum baseline that was common, matched up to PCI and included both firewalls and AV.
Does this mean that compliance dictates security purchases? Well, it’s definitely a contributing factor. Other spending models that many enterprises adhere to include benchmarking, metric-driven or evidence-driven.
Other informal methods that are often seen in organizations that have lower security maturity include spending the minimum needed until the next breach/incident. Or conversely, spending until the budget has been exhausted.
Rick Holland (formerly Forrester) coined the phrase ‘expense in-depth’ to illustrate how many organizations will spend money on the latest and greatest technologies with the false promise of ‘defense in depth’. However, this often leads to overspending in some areas and underspending in others.
An interesting perspective was presented by Sounil Yu at the RSA conference in which he presented a cyber defense matrix based on asset classes (devices, apps, networks, data, users) against operational functions (identify, protect, detect, respond, recover).
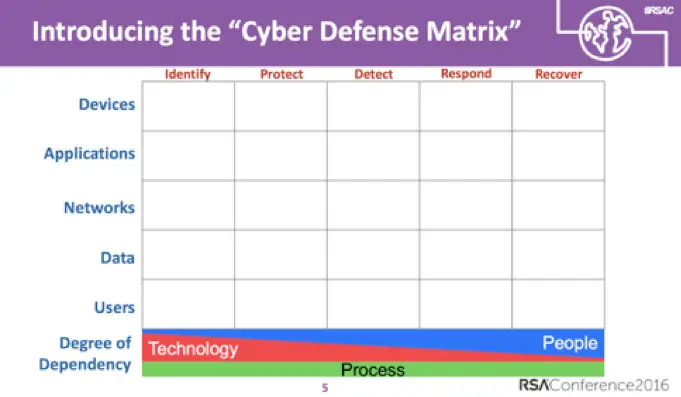
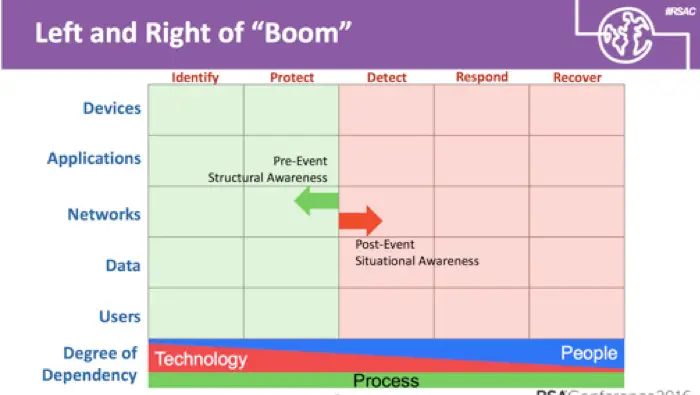
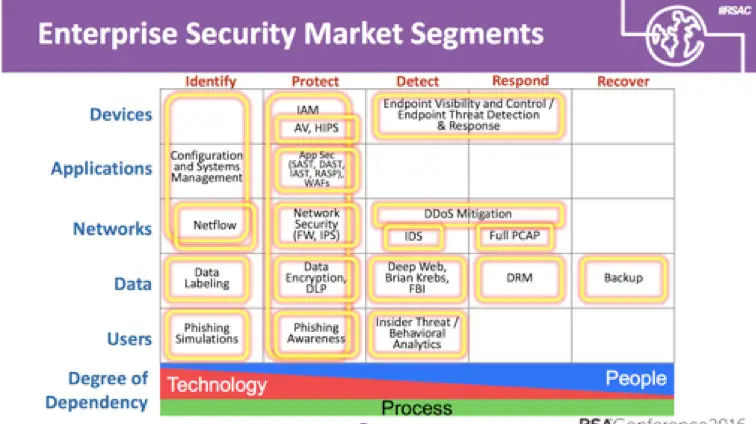
While this is not a perfect model, it could definitely help enterprises evaluate the entire portfolio and match up where deficiencies lie, or where there is considerable technology overlap.
Dump them!
Organizations are often poor at dumping security products they no longer need. Security products are not immune to the same issues that face other legacy systems — vulnerabilities, bottlenecks or performance issues can exist.
In fact, according to the Veracode State of Software Security Report, security products fail in 74% of test cases. Does your organization really need that kind of liability?
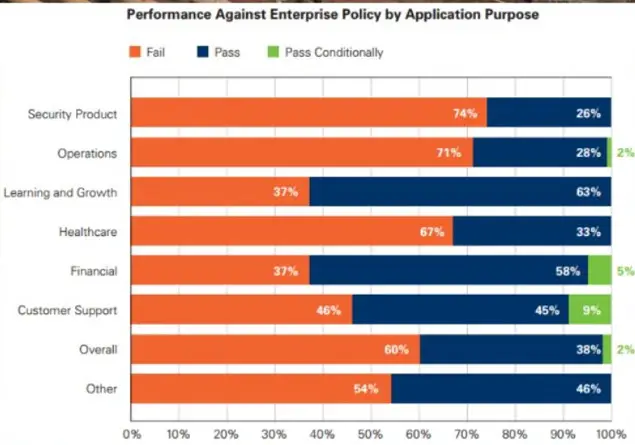
More than that though, redundant security products can hinder future purchases. Having a redundant endpoint security agent can prohibit the installation of a newer, more appropriate endpoint security technology because on paper at least, the control exists.
Security shelfware compounds to the issue, where an enterprise may purchase a security product but never get around to fully implementing it or gain its full benefit – therefore ending up on the shelf.
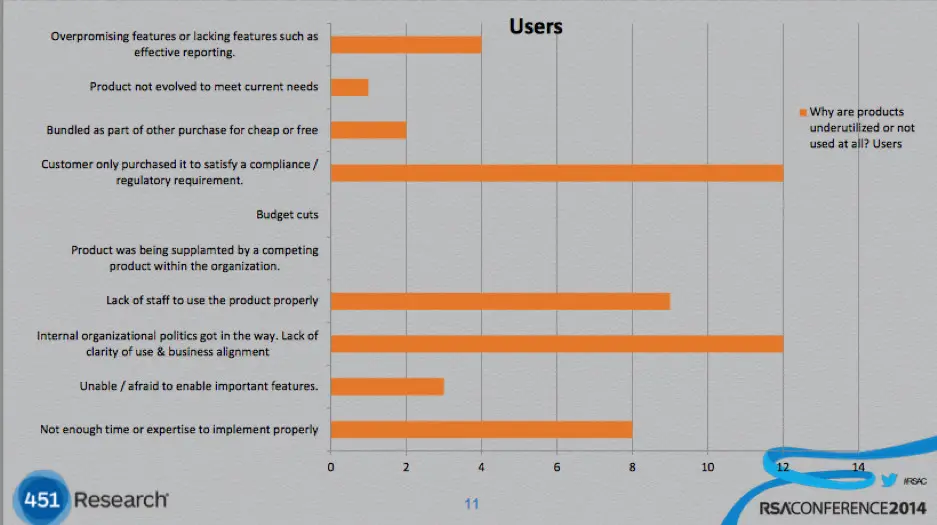
Many times, blinded by shiny new products, enterprises can overlook the capabilities already present within the products they have. So rather than buying another tool, it’s better to trim and streamline the existing portfolio. This not only improves performance, but results in better integration, communication, and ultimately price.
For this reason, comprehensive security platforms that have a multitude of features can often work out far better in the long run when compared to point products.
Confusing a crush for true love
Simply spending on security technologies is not enough. While purchasing a technology alone can lead to shelfware, there is another side effect whereby throwing resources at security technologies without a proper plan can result in staff ending up very busy – but not necessarily productive.
For example, conducting regular vulnerability scans is a good idea. Organizations should know where their vulnerabilities exist. But merely investing in a tool and generating a report every month is not enough. It will simply be an expense that will keep staff tied up in generating reports. Rather, enterprises should look at the quality of output and what progress is being made towards accomplishing security goals.
While the temptation may be to invest in a security technology that produces nice graphics and metrics, it can sometimes be as useful as an umbrella that reports how many raindrops it has stopped.
So, it’s best to tie security technology investments back to overall objectives and to regularly check to ensure they are contributing towards those objectives, not just as individual products, but as part of the wider security portfolio.
Put a ring on it
There is no well-established right or wrong security product investment strategy, just like there is no right person to marry.
But it’s important to consider what the overall objectives are, and where the biggest threats to your organization come from. Sure, it may be that a security product is amazing at what it does. But if it doesn’t solve a problem for you, then why commit to a multi-year contract?
Similarly, look at how much you’ll have to put into any commitment. Will the success of the product rely on you throwing considerable resources at it, including external consultants to get it working properly? Or can you schedule and set things to run in an automated manner with a quick deployment?
It is also important that enterprises continually seek assurance that security investments are working as intended – and if not, have an exit process in place to be able to effectively remove the product and replace it if needed, so as to not leave redundant technologies muddying the waters.
When you are walking the floors of RSA or any other conference, and you’re being sweet-talked by a charming salesperson, ask yourself, is this a security product you really want to marry, date, or dump?
About the Author:
Javvad Malik is a Security Awareness Advocate at KnowBe4, a blogger event speaker and industry commentator who is possibly best known as one of the industry’s most prolific video bloggers with his signature fresh and light-hearted perspective on security that speak to both technical and non-technical audiences alike.
Prior to joining KnowBe4, Javvad was a Security Advocate for AlienVault and a Senior Analyst at 451’s Enterprise Security Practice (ESP), providing in-depth, timely perspective on the state of enterprise security and emerging trends in addition to competitive research, new product and go-to-market positioning, investment due diligence and M&A strategy to technology vendors, private equity firms, venture capitalists and end-users. Prior to joining 451 Research, he was an independent security consultant, with a career spanning 12+ years working for some of the largest companies across the financial and energy sectors. As well as being an author and co-author of several books, Javvad was one of the co-founders of the Security B-Sides London conference.
In some of our articles and especially in our reviews, you will find Amazon or other affiliate links. As Amazon Associates, we earn from qualifying purchases. Any other purchases you make through these links often result in a small amount being earned for the site and/or our writers. Techaeris often covers brand press releases. Doing this does not constitute an endorsement of any product or service by Techaeris. We provide the press release information for our audience to be informed and make their own decision on a purchase or not. Only our reviews are an endorsement or lack thereof. For more information, you can read our full disclaimer.
Last Updated on February 3, 2021.










