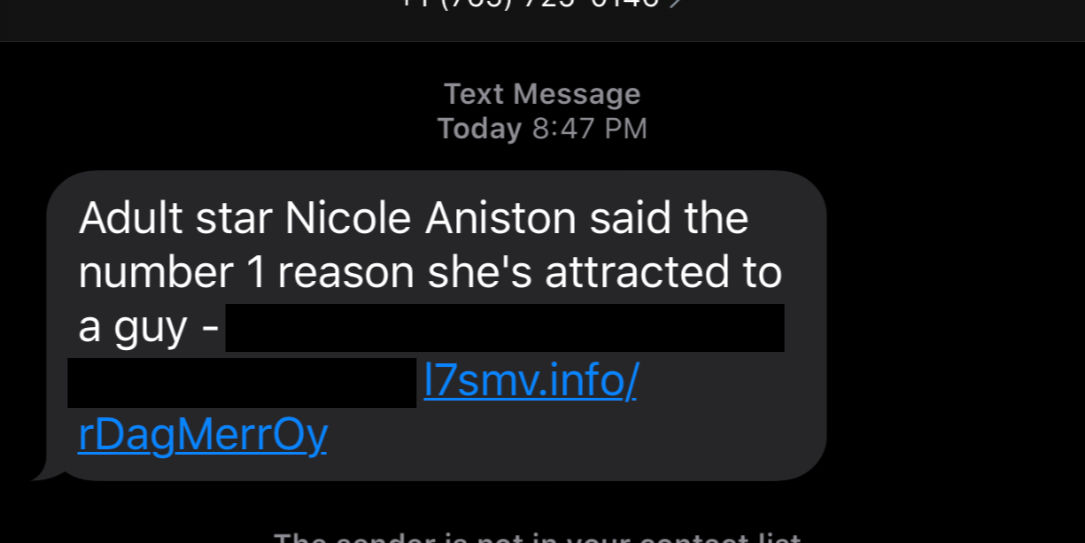
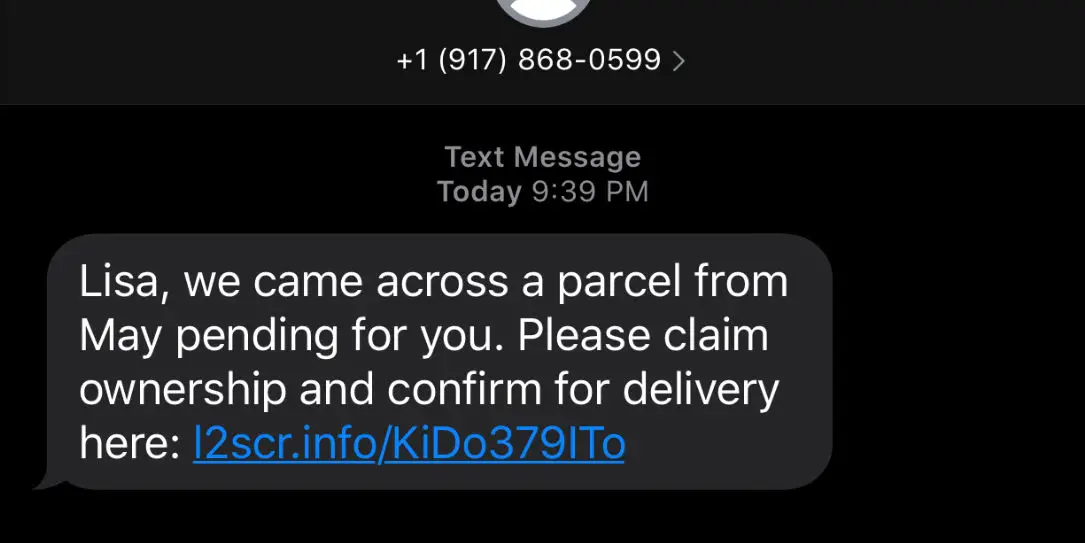
Here are five cybersecurity measures a small business can use to safeguard its online presence
Protecting your small business’s online presence is essential to maintain customer trust; here are five cybersecurity measures a small business can implement.